SAML Authentication Configuration
This document outlines the steps to configure SAML authentication for Pulse-IT and Automate-IT.
Prerequisites
Setting up the Identity provider - Azure Entra ID
Create the custom application
- Go to Entra ID
- Go to Enterprise applications
- Click on "New application"
- Click on "Create your own application"
- Name your app and chose "Integrate any other application you don't find in the gallery"
- Click on "create"
Grant access to users and groups
- Go to Users and groups
- Click "Add user/group"
- Select the users and groups
Configure SSO
- Go to Manage > Single sign-on
- Click on SAML
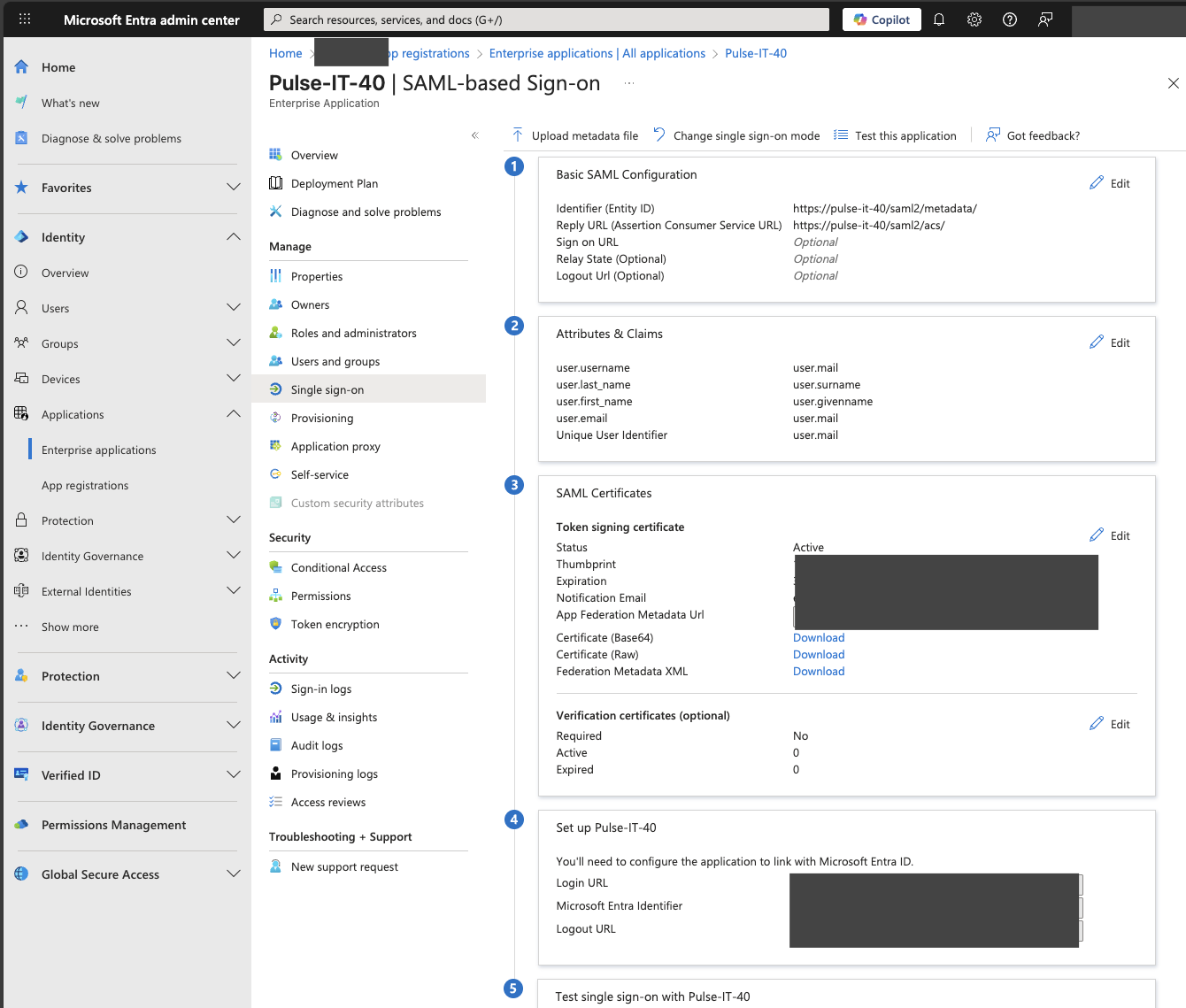
- Edit "Basic SAML Configuration"
- Add the identifier - https://replace-with-your-pulse-it-url/saml2/metadata
- Add the Reply URL (Assertion Consumer Service URL) - https://replace-with-your-pulse-it-url/saml2/acs
- Save
- Edit "Attributes and Claims"
- Edit "Unique User Identifier (Name ID)" in "Required claim", and enter in "Source attribute": user.mail
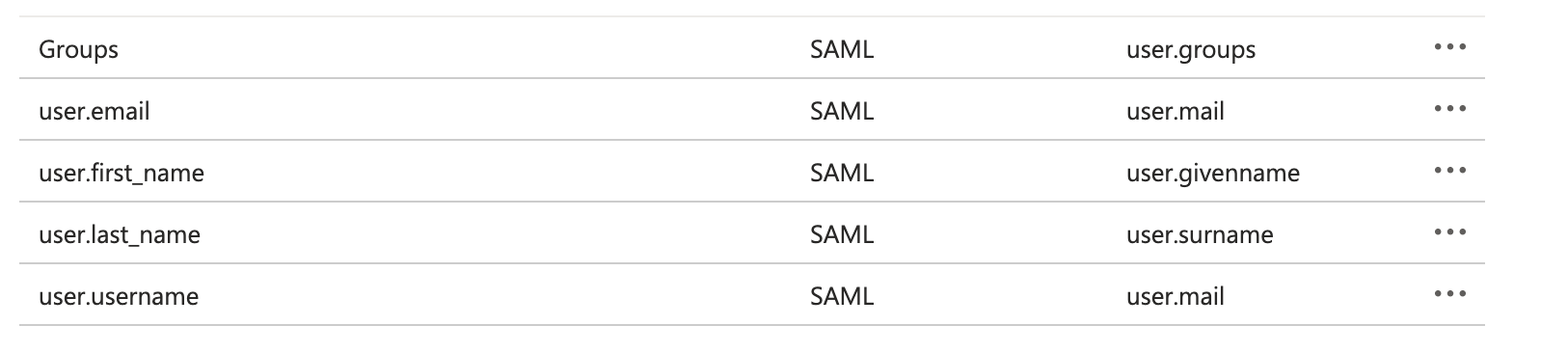
- Edit the "Additional claims" so you get the following
- Groups - user.groups
- user.email - user.mail
- user.first_name - user.givenname
- user.last_name - user.surname
- user.username - you can chose the field that makes most sense for you, it can be user.mail, or any other attribute coming from your IDP
- Note: Pulse-IT and Automate-IT will display as user login in the header, "last_name" and "first_name", or "username" if they are empty
1. Configure Pulse-IT for SAML
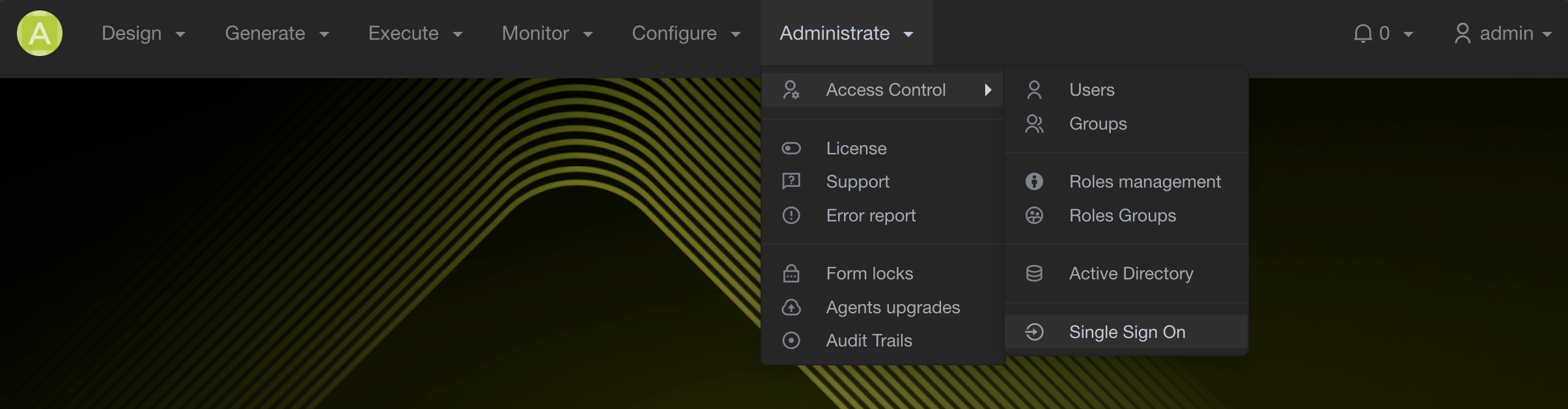
Navigate to Single Sign On Settings
- Log in to your Pulse-IT or Automate-IT instance with an admin user.
- Navigate to the Administrate menu.
- Under Access Control, click Single Sign On.
Add a new SAML Provider
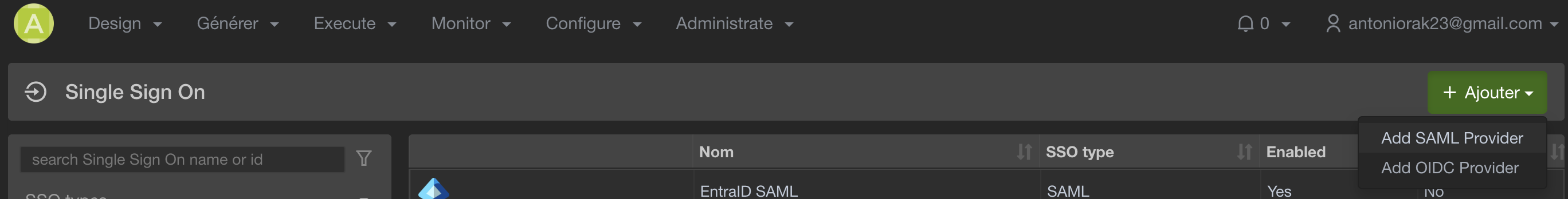
- On the Single Sign On page, click the + Add button.
- Select Add SAML Provider from the dropdown menu.
Configure SAML Provider
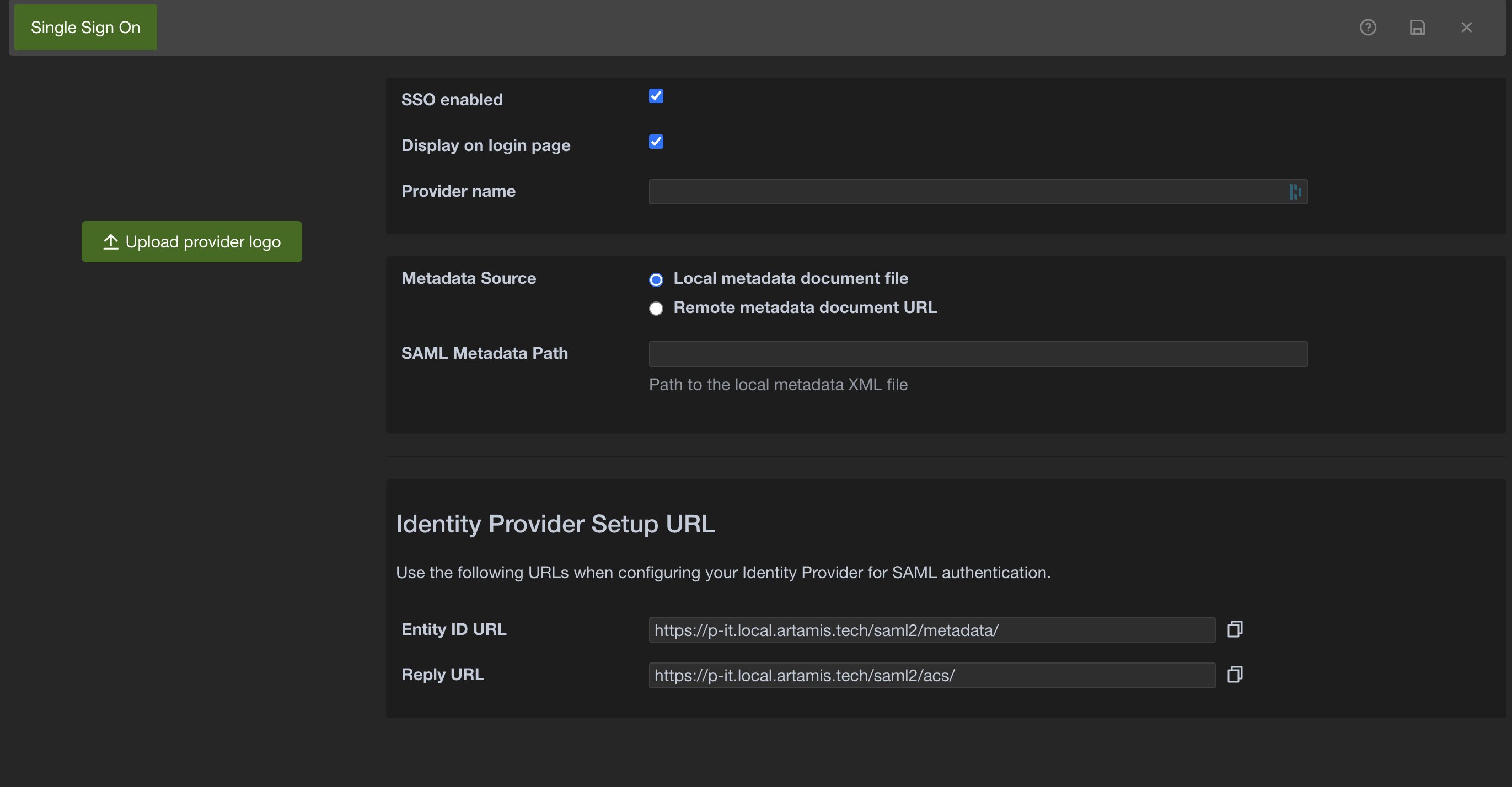
The following fields are available when configuring a SAML provider:
-
SSO enabled:
Enable or disable this specific SAML Single Sign On configuration. When enabled, users can authenticate using this provider. -
Display on login page:
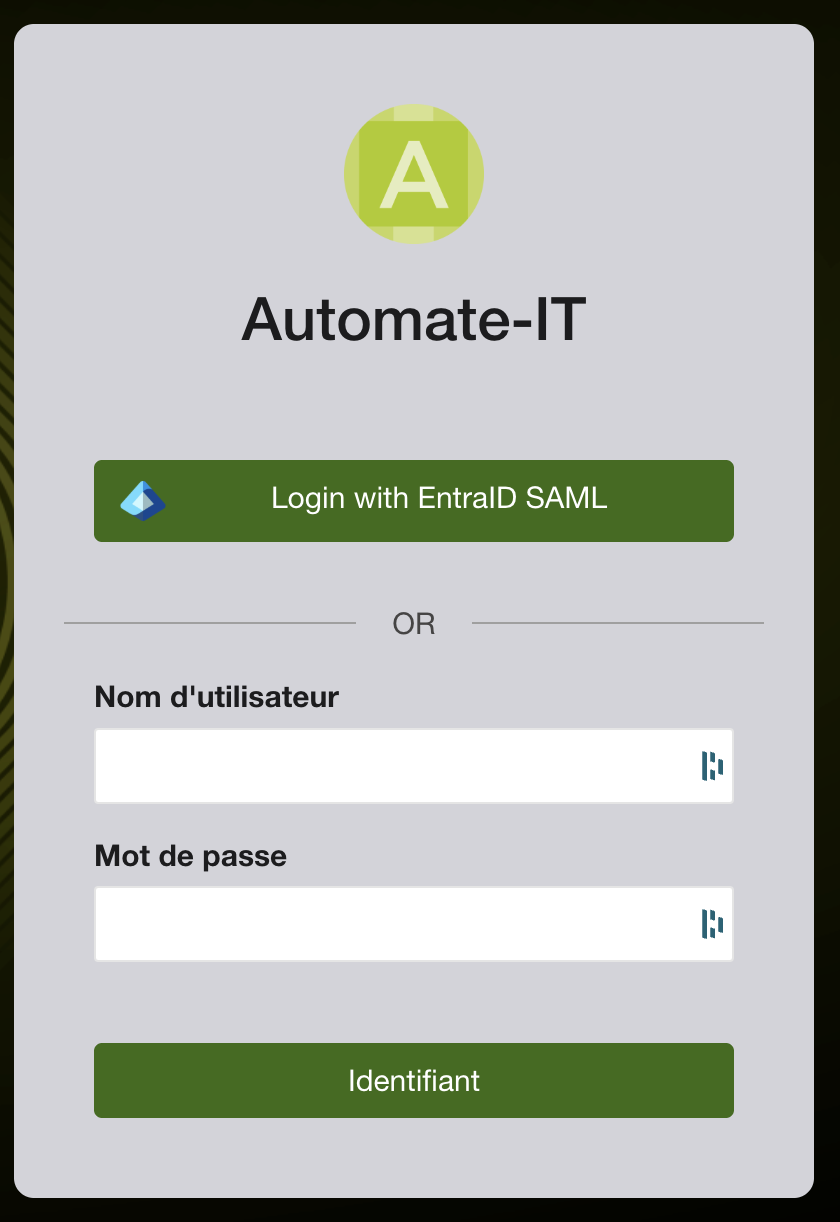
Determines if a button for this SAML provider is displayed on the login page of Pulse-IT/Automate-IT. If checked, users will see an option to "Login with [Provider Name]". -
Provider name:
A user-friendly name for the SAML identity provider (IdP). This name will be displayed on the login page if "Display on login page" is enabled. -
Upload provider logo:
Upload a logo for the identity provider. This logo will be displayed alongside the provider name on the login page. -
Metadata Source:
This option specifies how Pulse-IT/Automate-IT should obtain the SAML metadata from your Identity Provider.- Local metadata document file: Select this if you have downloaded the IdP metadata XML file and want to upload it to Pulse-IT/Automate-IT. When this option is selected, the field name will change to SAML Metadata Path.
- Remote metadata document URL: Select this if your IdP provides a URL where the metadata XML file can be accessed dynamically. When this option is selected, the field name will remain SAML Metadata URL.
-
SAML Metadata Path:
Provide the local metadata XML file path containing the Identity Provider's SAML metadata. This option appears when "Local metadata document file" is selected. -
SAML Metadata URL: Enter the URL pointing to the Identity Provider's SAML metadata XML file. The application will fetch configuration details from this URL. This option appears when "Remote metadata document URL" is selected.
Note: The metadata URL using a self-signed certificate is not supported.
2. Configuring your SAML Identity Provider
Once you have configured the SAML provider settings in Pulse-IT/Automate-IT, you will need to configure your Identity Provider (IdP) using the information provided in the Identity Provider Setup URL section.
You will need the Entity ID URL and the Reply URL to set up the connection on the IdP side.
Refer to your Identity Provider's documentation for specific instructions on how to configure a SAML application using these URLs.
3. Entra ID (Azure AD) Example Configuration
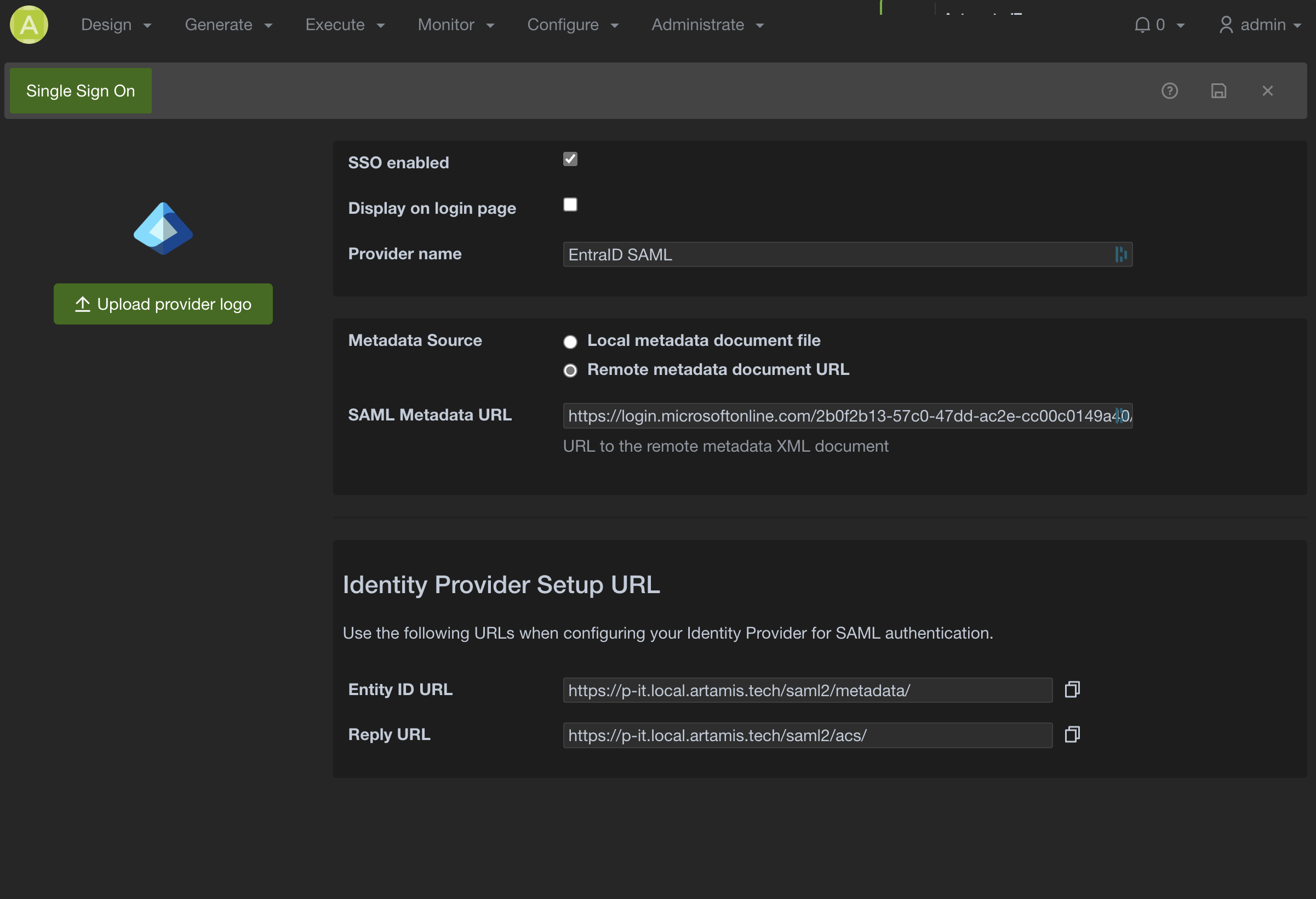
Here is an example configuration for setting up SAML authentication with Entra ID:
- Access Single Sign On settings in Pulse-IT/Automate-IT as described above.
- Click + Add and select Add SAML Provider.
- Configure the following fields:
- SSO enabled: Check this box.
- Display on login page: Check this box.
- Provider name: Enter EntraID SAML.
- Upload provider logo: Optionally upload the Entra ID logo.
- Metadata Source: Select Remote metadata document URL.
- SAML Metadata URL: Enter the Federation Metadata URL provided by Entra ID for your application. This typically looks like https://login.microsoftonline.com/\[Your-Tenant-ID\]/federationmetadata/2007-06/federationmetadata.xml.
- Copy the Entity ID URL and Reply URL provided in the Identity Provider Setup URL section. You will need these when configuring the application registration in Entra ID.
- Entity ID URL: [pulse-it-automate-it-address]/saml2/metadata/ (This will be specific to your Pulse-IT/Automate-IT instance URL).
- Reply URL: [pulse-it-automate-it-address]/saml2/acs/ (This will be specific to your Pulse-IT/Automate-IT instance URL).
- In the Azure portal, navigate to Microsoft Entra ID > App registrations or Enterprise applications and configure a new application registration for Pulse-IT/Automate-IT.
- In the SAML configuration settings within the Azure portal for your application registration, use the Entity ID URL as the Identifier (Entity ID) and the Reply URL as the Reply URL (Assertion Consumer Service URL).
- Configure user and group assignments in Entra ID to control which users can authenticate via SAML.
After completing these steps, you should see the "Log in with EntraID SAML" option on your login page, and users assigned to the application in Entra ID should be able to authenticate successfully.